Trusted Platform Module- Its Uses, and Implementation

Trusted Platform Module is an encrypting chip protecting hardware and software systems. In this blog we will discuss its uses, implementation, and benefits.
Now, let’s discuss below what is trusted platform module!
What is Trusted Platform Module (What is TPM)
Trusted Platform Module is a security-enabled device/chip. The design of the device supports the security of various related devices and software’s with password encryption. The encryption of confidential information is very necessary in this digital era. This is possible with the hardware solution having computer-generated keys.
The TPM secures the sensitive data, passwords, and encryption keys recorded on the system. Each Trusted Platform Module has unique identity stores as signature and needs an owner to use. The major supports of this security device are:
- Asymmetric generation of key.
- Asymmetric Encryption and decryption of the confidential information.
- Generates random numbers.
 What is the Purpose of the Trusted Platform Module
What is the Purpose of the Trusted Platform Module
The major purpose of the TPM is to verify the integrity of the early boot components.
Uses of Trusted Platform Module
The Trusted Platform Module ensures the security of various computer assets. It was procured to support the department of defense in the United States. Department occupies this module for device identification, encryption, and verification of its integrity. To explain this more, let me describe all the uses of TPM as below:
Integrity of Platform
The most important function of TPM is to ensure the integrity of a particular platform over the internet or operating system. To ensure this functionality, TPM checks the process of booting and its authority via hardware and software systems. Thus, this asset acts as a firmware. It also contains configuration registers for storing and reporting the information securely.
Encryption of Disk
TPM provides utility to protect encrypted keys stored in storage devices on the computer system. It also checks and provides an authoritative path to the information system including booting and firmware processes.
Protection of Password

To authenticate the password is important to protect the computer system, data, and keys stored on it. So, the Trusted Platform Module just not ensure authentication in software because it will create a risk of a dictionary attack. Therefore, it also ensures hardware protection. Moreover, it allows for very complex and strong passwords only.
Some other uses
Trusted Platform Module has some other uses and functionalities as below:
- The application software uses TMP to manage digital rights.
- It ensures the protection and enforcement of various licenses for software.
- Along with this, it also prevents cheating in online games or programs.
How to Implement the Trusted Platform Module?
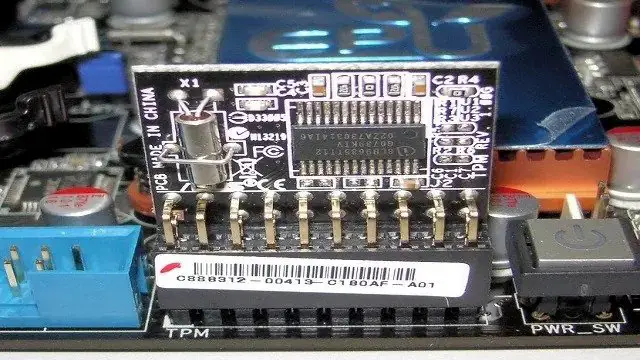
At the starting of this asset technology in the year 2006, the new laptops have been sold with in-build TPM. The asset is mainly co-located with the motherboard chip. But it has some other implementation types as well. These are mentioned below:
Types of implementation
Integrated Trusted Platform Module
As the name suggests TPM chip is co-locating with some other chip. So, it will resist bugs in software with the use of hardware itself. Therefore, there is no need to implement resistance tamper.
Virtual TPM
The type of TPM is mainly provided by the hypervisor. So, it always depends on it for the execution. Hypervisor allows the asset to execute independently and get the codes from the virtual machines using software.
Discrete Trusted Platform Module
The discrete trusted platform module is the specific dedicated chip. It implements the functionality in its own resistant temper of the semiconductor package. Therefore, it is more resistant to bugs in contrast to software. Thus, it is more preferable in all types of TPM.
Software TPM
Software TPM acts as simple software and does not provide any additional security to the system. It just responds as per the environment. The major problem in this type of TPM is it has the risk of its own bugs or attacks from the external software as well.
Firmware Trusted Platform Module
Firmware TPM is the solution type TPM that ensures a trusted execution environment in the CPU. The risk factors of this trusted platform module are bugs, Intel, AMD, and Qualcomm.
How to Uninstall Trusted Platform Module?
To use a Trusted Platform Module, you need to install and configure it in a good manner as mentioned below:
- Firstly, there is a need for physical installation. Find the port of TPM on the motherboard and insert the module into it.
- The module has been installed. Now, you need to enable it for BIOS.
- After enabling, you will get into the windows. So, now run the software.
- When the installer pop-ups appear. Just click next and next.
- Accept the terms and conditions mentioned.
- Now, the pop up will ask for the name and location. Choose any.
- You can customize the services as well.
The software has been installed and enabled now. So, it’s time to configure the BitLocker.
- Go to the start menu.
- Click on the button naming ‘control panel.’
- Now, from the control panel page, click on BitLocker device encryption.
- Turn on the BitLocker for starting its operations.
- You will get the access prompt.
- Click on (used disk space only) and press next.
- The next pop-up or prompt will ask for the permission. Click on start encrypting.
- Finally, the encryption of your files is done.
Now, let’s move on the next section that is advantages and disadvantages of TPM.
Advantages of Trusted Platform Module
The Advantages of Trusted Platform Module are:
- The main and the most important advantage of TPM is it secures the confidential information.
- It provides authentication features in both software and hardware.
- The security is improved with this asset because it does not depend upon a software-based operating system.
- If you want to use TPM on a mobile phone, then you can encrypt the entire hard drive of your phone.
- Now, if you think about how you can share this data with your peers or the server. Then you can use a time certificate.
Along with protecting the information, TPM also provides hardware-oriented benefits as mentioned below:
- It records and reports the hardware functionality data.
- Moreover, it provides input to improve the booting, operating system, and BIOS.
- It also allows direct anonymous attestation to ensure the privacy of the system from various users.
- Most importantly, the architecture of TPM is cost-effective.
These are the benefits of Trusted Platform Module.
Disadvantages of Trusted Platform Module
In contrast to the advantages of TPM, there are also many TPM disadvantages as follows:
- The major disadvantage of TPM is it has the risk of bug.
- TPM does not protect the system from a cold boot attack.
- TPM just provides security against theft of the system. Contrarily, it does not consider online threats and attacks on the system or information stored.
- The process of its functioning is very long, as its tools run key finders until the right key works.
- Some studies also show that, while rebooting the system. TPM recovers the encryption key while the system connects to the external drive. Meanwhile, the hacker can decrypt the disk easily.
- Moreover, sometimes it shows a problem in connecting or running the right software.
These are the Trusted Platform Module (TPM) Advantages Disadvantages.
Application of Trusted Platform Module
Besides PCs, trusted modules can be employed in mobile phones and network equipment.
General FAQs
Do I have TPM in my system?
To check whether you have a trusted platform module application on your system or not, press windows+ R. The Run dialog box will appear. Now, search TPM. Enter the launch button. So, if you see the information about TPM on your computer. This means you have this application or otherwise.
What do you mean by the trusted platform Module malfunctioned?
This is the error message related to the functioning of TPM. If it appears on your screen, you need to check if your TPM is working properly. Sometimes, it shows when you try to clear TPM by taking backup. Consequently, the application reset the setting to default.
Can I install TPM on windows 10?
Yes, you can use the Trusted Platform Module on Windows 10. But the version should be 1507 only.
How to clear TPM?
To clear the data from TPM, follow the steps mentioned below:
1. Open the windows application naming Defender security center.
2. Click on device security.
3. Click on the Details button.
4. Now, click on security processor troubleshooting. And,
5. Finally click on clear TPM.
6. You need to restart your system now and you are done.
Conclusion
TPM supports hardware and software to protect confidential data. It provides a solution for various data encryption and protection problems. But, you must also know that the Trusted Platform Module is not globally accepted. Some countries have restricted the use of TPM for example China.

