What is VPN Concentrator – How it works & Protocols

VPN concentrator is sort of networking device that offer secure connection and deliver messages and data between VPN nodes. It is type of router that established virtual private network for large network infrastructure to implement secure and flexible remote work policy. It is supported by popular secure network protocols – IPSec and SSL protocols.
In the technological world today, there is a myriad of options that can be implemented to secure network connection which is paramount for a business. A business or corporation has a high probability of remote employees from different parts of the location. While working with employees at the pace of home, a business needs assurance that whatever shared resources, corporate information, and data are shared back and forth should be safe and secure. The role of VPN and VPN connectors come into the limelight.
What is a VPN?
VPN or Virtual Private Network gives you a secure connection from another network over the Internet. VPNs are built to access region-restricted websites and protect your browsing activity and much more. Usually, VPN allow you online privacy and browse through anonymity by establishing a private network from a public Internet connection. The encryption and anonymity defend your online activities, shipping, paying bills, and much more.

If you have established a private VPN Network, you are gaining more rewards of accessing your business or home files remotely. VPN has been proved beneficial for many entrepreneurs who can access files on the safety of home without getting attacked by third parties. Beyond all this, there comes a time when somewhere lacks and needs to upgrade the system for accessing files from any part of the world. This raises the demand for VPN connectors.
If you have been implementing a VPN router, you must consider a VPN concentrator as a better option. In this guide, we have concentrated everything from ABC of VPN concentrator to its importance and usage. We have enlisted the pros and cons of devices, it’s working, and upgrading it.
What is VPN Concentrator
Your business team is working on certain projects remotely at the pace of your home or different locations. The project work must be accessible to every member while also prioritizing confidentiality for others. VPN won’t be a good option as you need to install different VPNs. At this juncture, VPN concentrators can dive into scenarios to fulfill your demands.
Using VPN, all team members can get connected with the help of an internal network established for the project from any remote location through multiple VPN tunnels. VPN concentrators give you the freedom to establish secure connections through private tunnels to thousands of users at the same time. This process is enhanced to spread over the world without negotiating on security. Through a VPN concentrator, each of the employees can access their work files and work on their tasks given.
VPN concentrators work as a router that allows you to access multiple VPN tunnels to operate independently as well as connect to the network. Concentrators are specifically designed for creating and managing the VPN communication framework. It is designed to encourage communications between different VPN nodes.
VPN routers have limitations with the number of people that can access networks simultaneously. While VPN concentrators are a special type of router, that gives you the freedom to hundreds and thousands of users to access work at the same time without any hassle.
It offers data encryption and decryption, secure private tunnels, end to end data delivery, user authentication, and much more.
In case you are wondering why to invest in a VPN concentrator instead of a VPN router, then the answer is simple. To manage hundreds and thousands of choices you make, a VPN concentrator is the best choice.
Functionalities Supported by VPN Concentrators
- It forms a secure network tunnels
- Authenticate the remote user to access a central server
- Arrange and define the tunnel permutation and parameters
- Encrypt as well as decrypt data and information transmitted.
- Manage security keys associated with VPN networks
- Optimized flow of data packet traffic throughout various tunnel connections established
- Manage inbound and outbound traffic at endpoints.
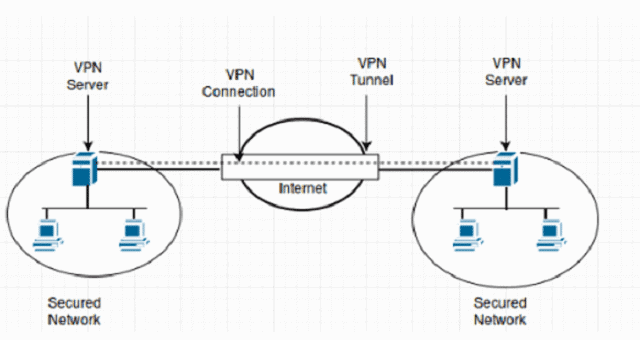
As per your business or company requirement, VPN concentrators can be deployed in different ways and formats, keeping into consideration remote users and ways of security. A diagram mentions you about traditional configuration, VPN concentrator sets up.
How does VPN Concentrator Work?
From different parts of the world, users access the internet. The traffic received is redirected and reshaped with the help of a VPN concentrator Firewall. Once the encryption process completes, the data or request are sent to the business server.
When the traffic returns back to the device, it is sent to the VPN concentrator that encrypts it and sends it back to the encrypted tunnel. This tunnel is either formed instantly or appears on request.
When you open up the software, there is a tunnel created automatically leading to a VPN concentrator for receiving any data passing through it. Some have the option of Always On, so you always receive data through an encrypted tunnel via a VPN concentrator.
VPN is established to monitor and operate thousands of clients remotely through encrypted VPN tunnels. In large institutions or businesses, employees can use concentrators to log on servers remotely at the same time.
Many small businesses do not implement proper precautions to their networks which eventually leads to loss of confidential data or data being hacked. VPN is created to provide security and encryption to business.
VPN Concentrator vs VPN Router
Both devices have the same working but different in many other ways. A concentrator can operate on thousands of VPN clients creating ideal corporate environments where the employees can reliably access private networks remotely.
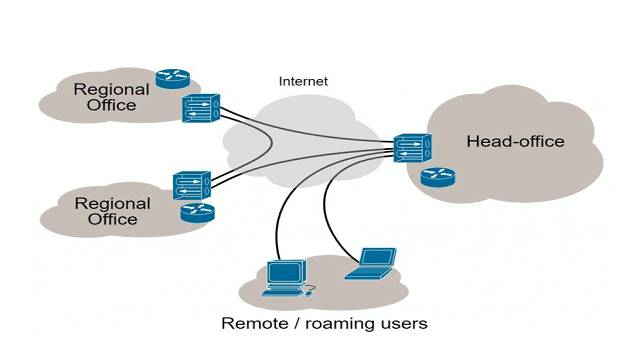
While on the other side, VPN concentrators do not make sense for using at home. It is not the right investment to buy and install a device unless your home is a top-level government or private office with a lot of business secret data.
Routers can be used for home and other small businesses where there is a limitation to access private networks. VPN routers are cheaper compared to concentrators and you would mostly get all features like USB ports, Ethernet ports, wireless connectivity, and much more.
The difference between VPN routers and VPN concentrators is the magnitude of the tasks they execute.
Why should a Business Invest in VPN Concentrator
The vitality of VPN concentrators in Small businesses or huge ones cannot be overemphasized. We have enlisted some of the reasons why companies should incorporate VPN concentrators.
Secured private network
Some companies require high-grade security for their ultra-sensitive data or documents. To avoid being hijacked by third parties or leaking to unauthorized people, some firms decide to preserve them on technology that allows them to access private networks remotely.
The issues with the remote desktop are easier for hackers to crack, but with a VPN concentrator, the story is different. VPN concentrator uses dynamic IP that makes it difficult for third parties to break private networks as the IP address keeps morphing every time you log in.
Unlimited Network Access
For companies where they need to accommodate all employees simultaneously, a VPN concentrator is the best solution. It gives access to hundreds and thousands of employees to connect on a network simultaneously without any issues.
Server Access
Whereas routers have limited access to company servers, VPN concentrators offer employees access to company servers from anywhere around the globe.
Which VPN Concentrator to Choose – IPSEC or SSL?
For encrypting files there are major two security protocols – Internet protocol security, Secure socket layer.
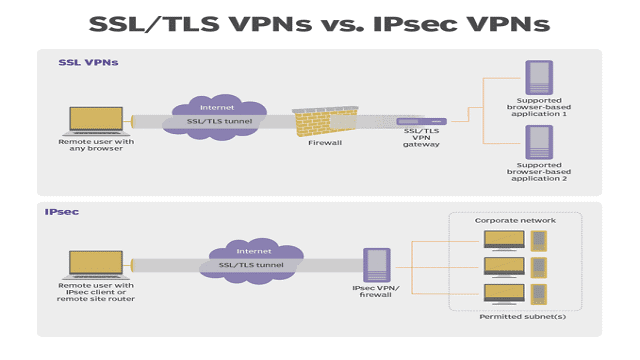
IPSEC or Internet protocol security encrypts files requiring client software to acquire private networks. IPSEC needs more technical skills and hours to configure but it results in two major advantages – high-level security – local address and security layers.IPSec encryption limits to a fixed remote location. In case, you are establishing a network on your home, you cannot use it on your restaurant WiFi or other.
Though IPSec Encryption is highly secure, it’s tiresome to configure it.
SSL or Secure Socket layer offers more versatility compared to counterpart. There is no software required for configuration and it is not limited to fixed remote locations. SSL may not offer a high level of security, it means users can access private networks from any location once they are connected to the Internet.
Conclusion
A VPN concentrator is the most sophisticated networking tool. They typically land up in one of two architectures – SSL or IPSec. If you require a single device to handle a large number of incoming tunnels, then VPN concentrators are the best choice.
Before diving into setting up an encryption protocol for your small business or corporate environment, you should consider your business needs, budget, and determine the best-suited solution for your business.
Once you have understood your business needs, a VPN concentrator can offer you different solutions to secure your server and protect them from outside invasive attacks.
